Ethical Hacking: Techniques and Best Practices in 2024
Ethical hacking, often referred to as penetration testing or white-hat hacking, plays a crucial role in identifying and fixing vulnerabilities within systems and networks. Here’s a look at some of the key techniques and best practices employed in ethical hacking today:
-
Understanding the Scope and Goals:
- Scope Definition: Clearly define the targets and limitations of the ethical hacking exercise to avoid unintended disruptions.
- Goal Setting: Establish specific objectives such as identifying security weaknesses, testing defenses, or ensuring compliance with security policies.
-
Reconnaissance and Information Gathering:
Ethical hackers begin by gathering information about the target system or network:
- Open-Source Intelligence (OSINT): Utilize publicly available information to gather details about the target, such as domain names, IP addresses, and organizational structure.
- Network Scanning: Conduct scans to discover active hosts, services running on them, and potential vulnerabilities.
-
Vulnerability Assessment and Analysis:
Once initial information is gathered, ethical hackers perform a comprehensive assessment:
- Automated Tools: Utilize tools like Nessus, OpenVAS, or Nmap to identify known vulnerabilities.
- Manual Testing: Conduct manual testing to discover complex or emerging vulnerabilities that automated tools may miss.
-
Exploitation and Reporting:
- Exploitation: Attempt to exploit identified vulnerabilities to demonstrate their potential impact.
- Documentation: Thoroughly document findings, including steps to reproduce vulnerabilities and their potential risks.
- Reporting: Prepare a detailed report for stakeholders, including technical teams and management, outlining discovered vulnerabilities and recommended mitigation strategies.
-
Continuous Learning and Improvement:
- Staying Updated: Keep abreast of the latest security trends, vulnerabilities, and exploitation techniques through continuous learning and participation in ethical hacking communities.
- Skill Enhancement: Regularly practice hacking techniques in safe environments to maintain and improve skills.
-
Compliance and Ethics:
- Adherence to Legal and Ethical Standards: Ensure all activities align with legal requirements and ethical guidelines, respecting privacy and confidentiality.
- Permission and Consent: Obtain appropriate permissions and consents before conducting ethical hacking activities on any system or network.
-
Collaboration and Communication:
- Teamwork: Collaborate with stakeholders, including IT teams, developers, and management, to understand business goals and prioritize security measures.
- Effective Communication: Clearly communicate findings, risks, and recommendations in a non-technical manner to facilitate informed decision-making.
Effectiveness of Ethical Hacking
Organizations often leverage ethical hacking to complement internal security measures. Unlike internal testing, ethical hacking brings an outsider’s fresh perspective, crucial for identifying blind spots and potential threats that may go unnoticed.
Methods of Ethical Hacking
- Bug Bounty Programs: Companies like Apple run bug bounty programs where security researchers and ethical hackers report vulnerabilities directly. These programs cover categories like “lock screen bypass” and “elevation of privilege,” offering rewards ranging from $5,000 to $2 million for critical findings.
- Ethical Hacking Communities: Platforms like HackerOne facilitate fully managed bug bounty programs, engaging a community of security experts. These experts actively seek vulnerabilities in exchange for rewards, contributing significantly to improving overall cybersecurity.

- Independent Security Assessments: Independent experts, such as those recommended by Infosec Skills author Ted Harrington, provide invaluable insights through one-time or recurring security assessments. This external evaluation helps organizations maintain a robust security posture against evolving threats.
Top Ethical Hacking Tools in 2024
Ethical hackers rely on a variety of advanced tools to assess and strengthen cybersecurity measures. Here are some essential tools widely used for penetration testing, vulnerability assessment, and network security:
- Metasploit: Metasploit is an industry-leading framework for penetration testing and exploit development. Its extensive database of exploits, payloads, and auxiliary modules makes it invaluable for security professionals worldwide.
- Wireshark: Wireshark remains a cornerstone for network protocol analysis, offering precise insights into network traffic. Its user-friendly interface and powerful filtering options aid in troubleshooting and detecting anomalies effectively.
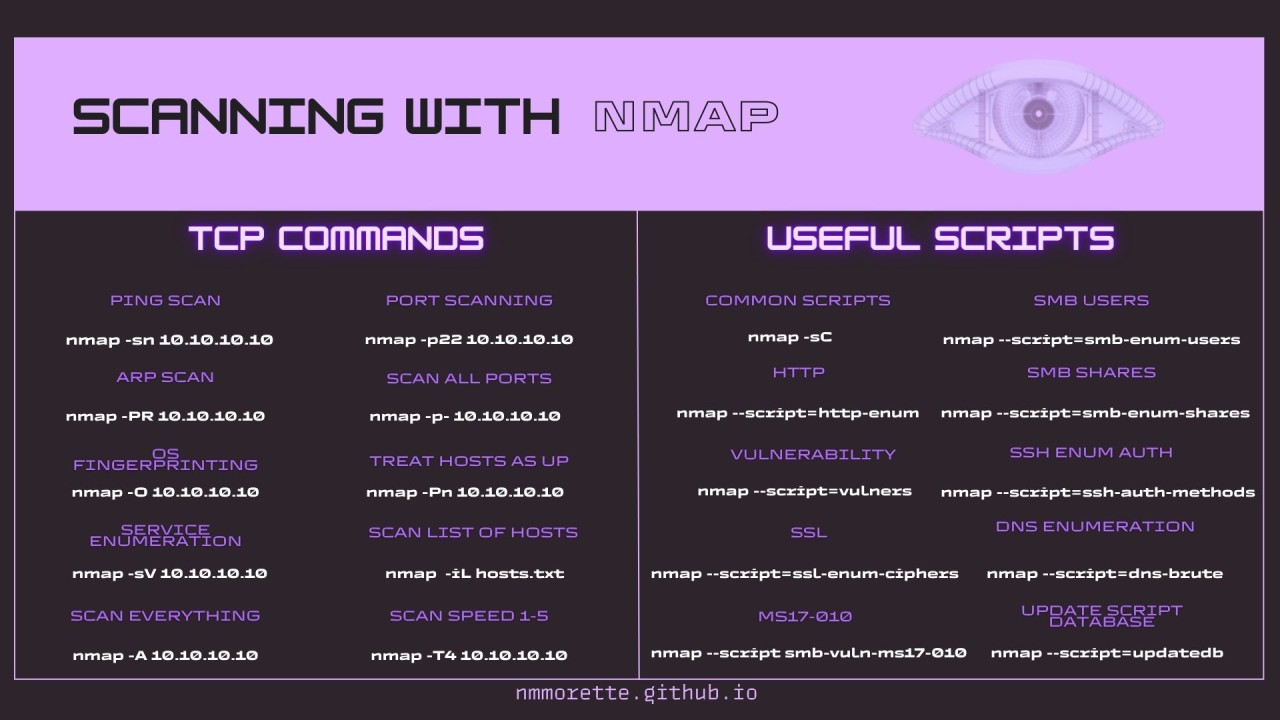
- Nmap: Nmap is essential for network discovery and vulnerability scanning. Its comprehensive scanning techniques, including host discovery and service enumeration, provide detailed insights into network security posture.
- Burp Suite: Burp Suite is renowned for its suite of web application security testing tools. From intercepting proxy to advanced scanning and intruder capabilities, Burp Suite helps in identifying and exploiting web application vulnerabilities comprehensively.
- OWASP ZAP (Zed Attack Proxy): OWASP ZAP is a popular alternative to Burp Suite, offering similar functionalities with a focus on automated scanning for web application vulnerabilities. It’s widely used for both manual and automated security testing.
- Hashcat: Hashcat excels in GPU-accelerated password cracking, supporting a wide range of hash types and algorithms. It’s particularly effective for breaking complex passwords and cryptographic hashes.
- Aircrack-ng: Aircrack-ng is essential for assessing and securing wireless networks. It includes tools for capturing packets, monitoring Wi-Fi networks, and performing WPA/WPA2 cracking to ensure robust wireless security.
- Maltego: Maltego revolutionizes digital forensics and intelligence gathering with its graphical interface. It’s used to visualize complex relationships across diverse data sources, aiding in reconnaissance and threat analysis.
- Hydra: Hydra is a powerful brute-force password cracking tool that supports various protocols and services. Its speed and flexibility make it ideal for penetration testers and security researchers assessing authentication mechanisms.
- Snort: Snort is an open-source network intrusion detection and prevention system (IDS/IPS). It’s widely used for real-time traffic analysis, packet logging, and threat detection in network environments.
These tools represent the cutting-edge in ethical hacking, empowering cybersecurity professionals to proactively identify and mitigate security risks in complex digital environments in 2024 and beyond. Each tool plays a vital role in ensuring the resilience and integrity of systems and networks against evolving cyber threats.
The Demand for Ethical Hacking
As cyberattacks surge, with a reported 38% increase year-over-year according to Check Point Research, the demand for ethical hacking has never been more critical. Industries safeguarding high-value or sensitive information, including healthcare, finance, manufacturing, and government sectors, are particularly vulnerable. This underscores the necessity for ethical hackers and robust training across industries to proactively identify and address vulnerabilities before malicious actors exploit them.
On the professional development front, training programs like Infosec’s Ethical Hacking Dual Certification Boot Camp, which prepares cybersecurity professionals for certifications such as Certified Ethical Hacker (CEH) and CompTIA PenTest+, remain popular. These certifications equip professionals with the skills needed to enhance organizational security and resilience in an increasingly digitized world.
Ethical hacking not only mitigates risks but also fosters a culture of proactive cybersecurity, ensuring that organizations remain resilient against evolving threats in 2024 and beyond.
Conclusion
Ethical hacking stands as a cornerstone in the defense against escalating cyber threats. By employing meticulous techniques, leveraging advanced tools, and adhering to ethical standards, ethical hackers play a pivotal role in fortifying systems and networks worldwide. As industries face ever-evolving challenges, the demand for skilled ethical hackers continues to grow, ensuring that organizations can proactively identify vulnerabilities and bolster their cybersecurity defenses. Embracing ethical hacking not only mitigates risks but also cultivates a culture of vigilance and resilience, crucial for navigating the complexities of digital security in 2024 and beyond.
Tag:Bug Bounty Programs, CEH Certification, CompTIA PenTest+, Cyber Defense, Cyber Threats, Cybersecurity, Cybersecurity Best Practices, Cybersecurity Training, Ethical Hacking, Ethical Hacking Techniques, Exploit Development, Information, IT Security, Network Protocol Analysis, Network Security, Penetration Testing, Security, Security Tools, Security Trends 2024, Vulnerability Assessment, White-Hat Hacking